Apple’s 6th minor update to El Capitan has left many photographers confused as to why they can no longer see 16-bit Tiffs in the finder or in Capture One. At first it seemed to be random what files were affected, but we soon realized that it wasn’t necessarily affecting small files but was always affecting large files.
Easily remedied for new outputs with a small change to your process recipe.
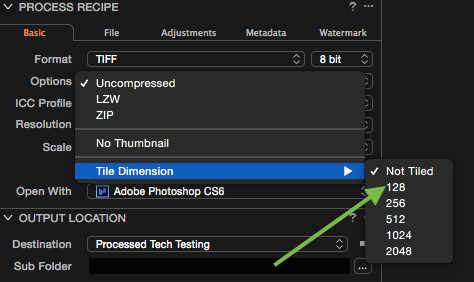
A TIFF image is usually saved as a whole, but may also be composed of a number of tiles. All tiles in the same image have the same dimensions and may be compressed independently of the entire image with the smaller tile size being able to be previewed within the OS and within Capture One.
Simply alter the options for TIFF output and change Tile Dimension from ‘Not Tiled’ to 128. Voilå.
The Backstory:
Talos, a member of Cisco’s Collective Security Intelligence ecosystem identified a vulnerability in Apple’s OS Image Core that would allow Apple Remote Code Execution With Image Files.
Per Talos on July 19th, 2016
“The Tagged Image File Format (TIFF) is a file format that is popular with graphic artists, photographers and the publishing industry because of its ability to store images in a lossless format. TIFF was created to try to establish a common scanned image file format in the mid 1980s. Cisco Talos has discovered a vulnerability in the way in which the Image I/O API parses and handles tiled TIFF image files. When rendered by applications that use the Image I/O API, a specially crafted TIFF image file can be used to create a heap based buffer overflow and ultimately achieve remote code execution on vulnerable systems and devices.
This vulnerability is especially concerning as it can be triggered in any application that makes use of the Apple Image I/O API when rendering tiled TIFF images. This means that an attacker could deliver a payload that successfully exploits this vulnerability using a wide range of potential attack vectors including iMessages, malicious web pages, MMS messages, or other malicious file attachments opened by any application that makes use of the Apple Image I/O API for rendering these types of files.
Furthermore, depending on the delivery method chosen by an attacker, this vulnerability is potentially exploitable through methods that do not require explicit user interaction since many applications (i.e. iMessage) automatically attempt to render images when they are received in their default configurations. As this vulnerability affects both OS X 10.11.5 and iOS 9.3.2 and is believed to be present in all previous versions, the number of affected devices is significant.”
Apple was obviously already on this as they released 10.11.6 a day before Talos published the piece that focused on 10.11.5.
So, this was no small fix for Apple and as a result we have only a small issue of workflow to deal with as a consequence of this security patch.